Welcome to the Emproof Nyx Demo Centre
Here you can try our IP Protection and Exploit Mitigation solutions, as well as our open-source assembler-disassembler Nyxstone coming soon.
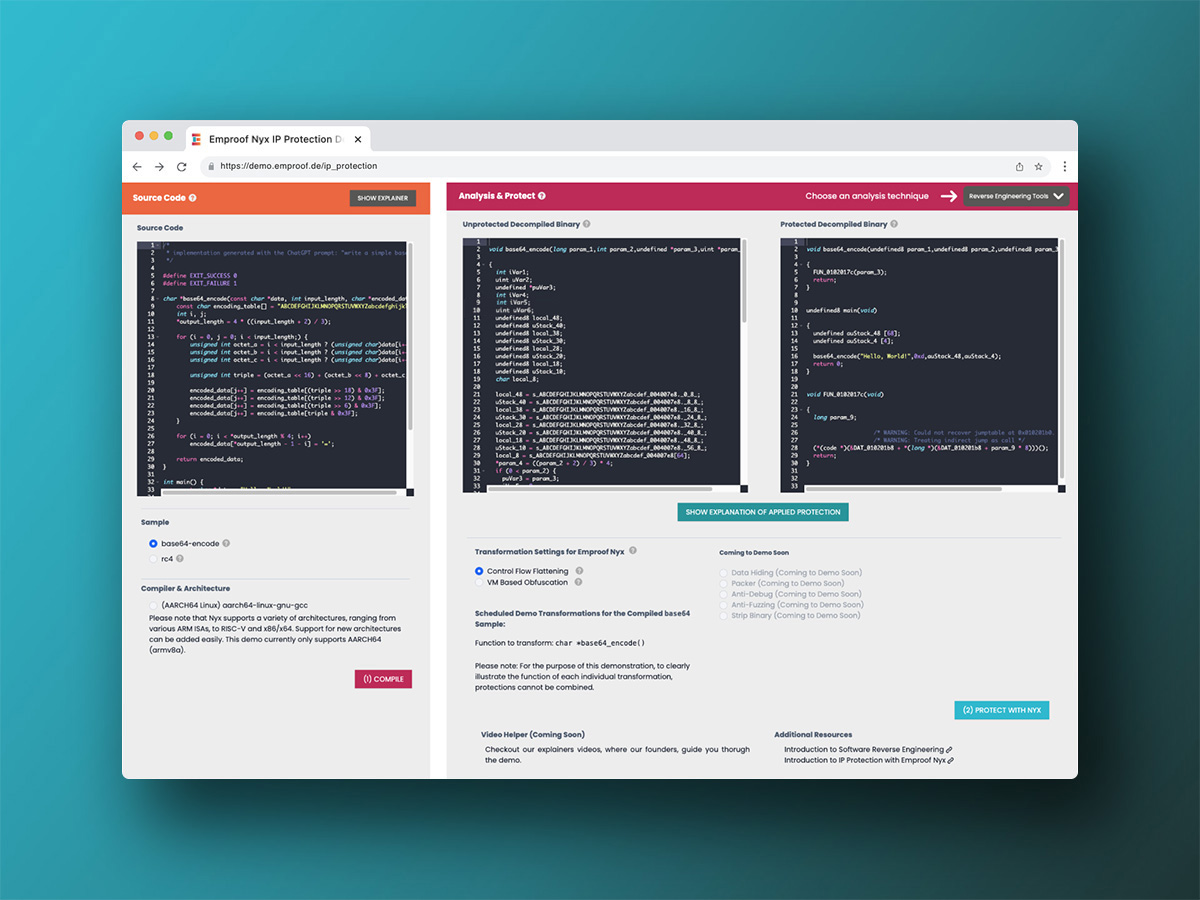
IP Protection Demo
IP Protection is essential for safeguarding your critical algorithms, code, and data from reverse engineering threats. In this demonstration, we will not only show you how Emproof Nyx can robustly protect your binary but also provide insights into the extensive range of techniques available to attackers for analysing binaries. Reverse engineering is easier and happens more frequently than is often perceived, so it is important to protect your binary.
IP Protection DemoExploit Mitigation Demo
In our Exploit Mitigation Demo, you will have the opportunity to execute a buffer overflow, one of the most prevalent types of vulnerabilities. Memory corruption issues, including buffer overflows, remain among the most common and easily overlooked security flaws. This demonstration will showcase how Emproof Nyx can effortlessly enhance your system's security against such exploitable bugs with just one simple click.
Exploit Mitigation Demo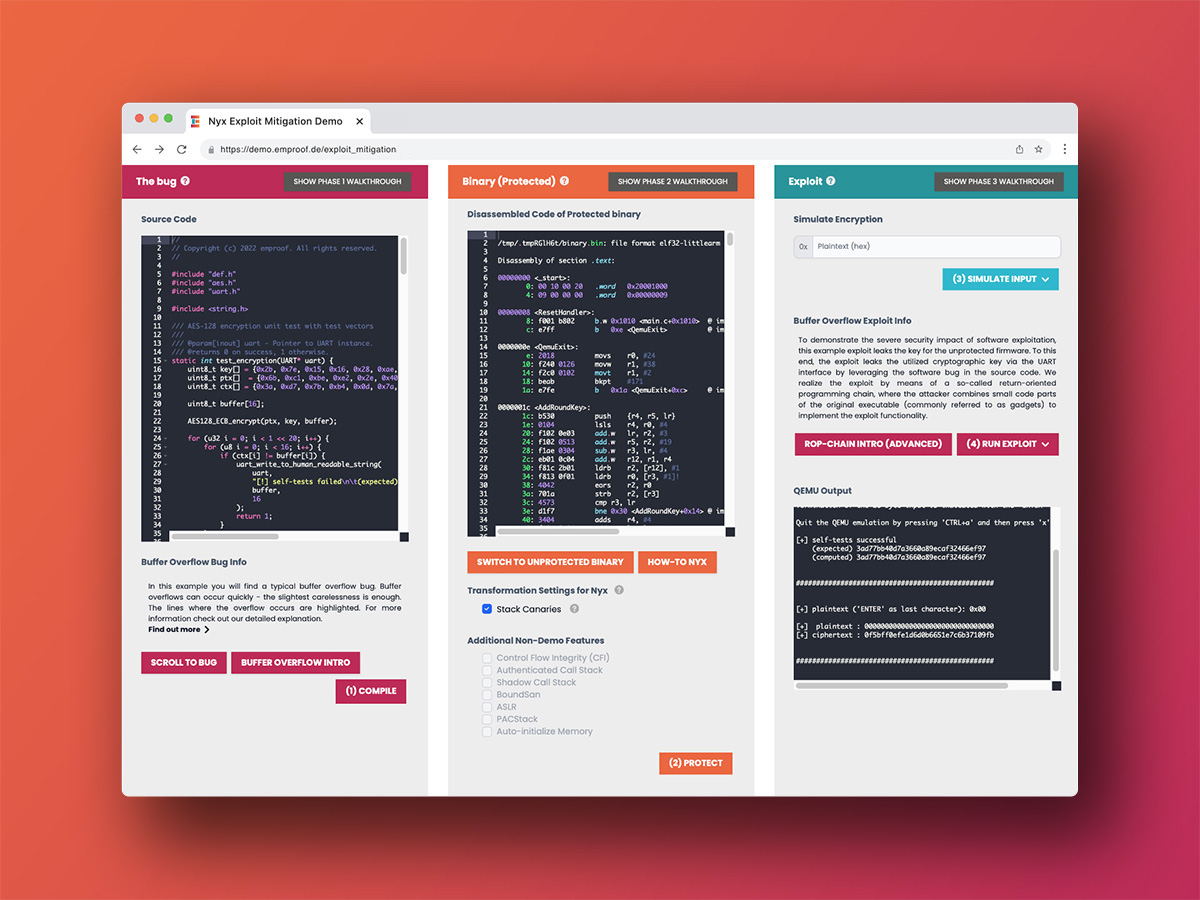
Resource Centre
If you want to get to know more about how our protection or software reverse engineering in general works, checkout our additional resources below.